Challenge Disclaimer
For this challenge, I went way more in-depth than I had to, basically ALL of what I found wasn’t useful for the beating the challenge, so if you want the actual solution, scroll to the bottom.
Challenge Info
Best Stuff - Cheap Stuff, Buy Buy Buy… Store Instance: source. The shop is open for business at nc mercury.picoctf.net 34938.
Connecting to the netcat listener
1 | > nc mercury.picoctf.net 34938 |
So, we have to figure out some sort of way to exploit this online “shop” (hence the challenge name). Since this is a reverse engineering challenge, let’s do some simple reconnaissance on the source file we’re given.
Gathering basic information
1 | > file source |
What this tells us about source:
- 32-bit file
- ELF (Executable and Linkable Format) binary
- LSB refers to Little Endian, so the least significant bytes are stored first, which is typical for Intel architectures
- Statically linked, so the binary includes all its dependencies and libraries within itself, meaning it’s all self-contained
- Not stripped, so it shouldn’t be missing any symbols or debugging information, making it easier to reverse engineer
Analyzing with Ghidra
Let’s put it through a reverse engineering tool, I’ll be Ghidra for this writeup, but you’re welcome to use whatever you prefer:
- Open Ghidra
- Make a temporary project
- Import the file into the project
- Double click the file, select “open in default tool”
The first thing I like to do is check the Symbol Tree, a hierarchical structure that displays symbols (functions, variables, classes, basically anything that’s an important identifier) within the analyzed binary. This is an important thing to know, as it’ll help you efficiently analyze.
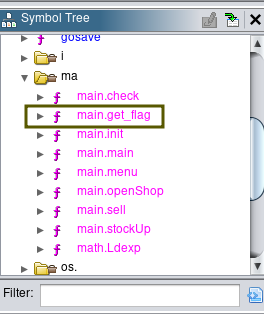
Instantly, we notice a function, get_flag. This can double click it to further investigate:
1 |
|
Some things to note:
io/ioutil.ReadFile,fmt.Println, andos.seem unusual for C, after some further research, I learned that:- All these functions originate from the Go programming language
io/ioutil.ReadFileis for reading filesfmt.Printlnis for printing to standard outputos.exitis for exiting the program
So, it’s clear that this is what reads our flag, if we can somehow call this, we’ll have our flag.
Let’s try and get the address for the get_flag function, we can do this by right-clicking get_flag in the symbol tree, and selecting “Show references to”. The one we want to pay attention to is the “call”, it should display that the location of it is 080d3ec3.
Solution
So, this challenge is a bit too easy for it’s own good. The actual solution is to just buy negative items to increase our coins, and then buy the flag.
1 | > nc mercury.picoctf.net 34938 |
Our flag is given to us in an encrypted format, so let’s run it through Cyberchef using the Magic recipe (make sure to remove the brackets!).
flag: picoCTF{b4d_brogrammer_ba6b8cdf}